Рабочая инструкция для домена creative-impulse.ru на Ubuntu 16.04 Server amd64, как изменить работу блога/сайта с http на https при использовании nginx + устанавливаем в шагах сертификат Let's Encrypt от и до.
Проверена от 04.02.2019 + применялись в 2020 году на Ubuntu 18.04 Server все работает.
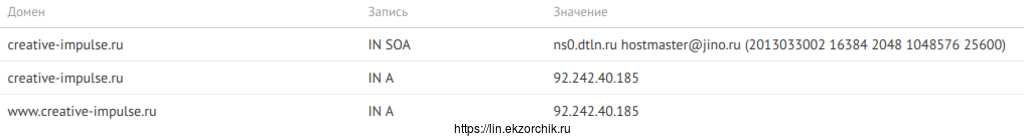
Шаг №1: На регистраторе доменного имени в свойствах DNS—записей должны быть созданы записи:
Шаг №2: Подключаюсь по SSH к VPS (CPU,HDD,RAM)
sudo chsh -s /bin/bash ekzorchik ekzorchik@Ubuntu1604-001:~$ hostname -I 92.242.40.150
Шаг №3: Изменяю доменное имя на хосте
ekzorchik@creative-impulse:~$ sudo nano /etc/hosts 127.0.0.1 localhost #127.0.1.1 Ubuntu1604-001 92.242.40.185 www.creative-impulse.ru creative-impulse.ru ekzorchik@creative-impulse:~$ sudo nano /etc/hostname creative-impulse.ru
Шаг №4: Устанавливаю в систему пакет Mercurial
ekzorchik@Ubuntu1604-001:~$ sudo apt-get install mercurial -y
Шаг №5: С учетом своих скриптов на собственном хранилище делаю преднастройку сервера
ekzorchik@creative-impulse:~$ hg clone --insecure https://ekzorchik@WAN-DNS-MY-HOME:PORT/hg/dproject ekzorchik@creative-impulse:~$ nano dproject/default #proxy ekzorchik@creative-impulse:~$ sudo ./dproject/default
Важно чтобы были прописаны настройки локали
ekzorchik@creative-impulse:~$ sudo ./dproject/default ekzorchik@creative-impulse:~$ sudo nano /etc/environment LANG=en_US.UTF-8 LC_ALL=en_US.UTF-8 ekzorchik@creative-impulse:~$ source /etc/environment
Шаг №6: Сперва разворачиваю через скрипт блог wordpress
ekzorchik@Ubuntu1604-001:~$ hg clone --insecure https://ekzorchik@WAN-DNS-MY-HOME:PORT/hg/wordpress ekzorchik@srv-xenial:~$ cd wordpress/ ekzorchik@srv-xenial:~/wordpress$ sudo ./swnginx_int.sh ekzorchik@creative-impulse:~/wordpress$ cd ~
Шаг №7: Создаю сертификат для доменного имени creative-impulse.ru и перенастраиваю конфигурационный файл nginx
ekzorchik@creative-impulse:~$ sudo wget https://dl.eff.org/certbot-auto -O /usr/sbin/certbot-auto ekzorchik@creative-impulse:~$ file /usr/sbin/certbot-auto /usr/sbin/certbot-auto: POSIX shell script, UTF-8 Unicode text executable ekzorchik@creative-impulse:~$ sudo chmod a+x /usr/sbin/certbot-auto
Запускаю в интерактивном режиме где на вопросы буду отвечать:
ekzorchik@creative-impulse:~$ sudo certbot-auto Bootstrapping dependencies for Debian-based OSes... (you can skip this with --no-bootstrap) Hit:1 http://security.ubuntu.com/ubuntu xenial-security InRelease Hit:2 http://us.archive.ubuntu.com/ubuntu xenial InRelease Hit:3 http://us.archive.ubuntu.com/ubuntu xenial-updates InRelease Hit:4 http://us.archive.ubuntu.com/ubuntu xenial-backports InRelease Reading package lists... Done Reading package lists... Done Building dependency tree Reading state information... Done ca-certificates is already the newest version (20170717~16.04.2). openssl is already the newest version (1.0.2g-1ubuntu4.14). python is already the newest version (2.7.12-1~16.04). python set to manually installed. The following additional packages will be installed: binutils cpp cpp-5 gcc-5 libasan2 libatomic1 libc-dev-bin libc6-dev libcc1-0 libcilkrts5 libexpat1-dev libgcc-5-dev libgomp1 libisl15 libitm1 liblsan0 libmpc3 libmpx0 libpython-dev libpython2.7 libpython2.7-dev libquadmath0 libtsan0 libubsan0 linux-libc-dev python-pip-whl python-pkg-resources python2.7-dev python3-virtualenv zlib1g-dev Suggested packages: augeas-doc binutils-doc cpp-doc gcc-5-locales gcc-multilib make manpages-dev autoconf automake libtool flex bison gdb gcc-doc gcc-5-multilib gcc-5-doc libgcc1-dbg libgomp1-dbg libitm1-dbg libatomic1-dbg libasan2-dbg liblsan0-dbg libtsan0-dbg libubsan0-dbg libcilkrts5-dbg libmpx0-dbg libquadmath0-dbg augeas-tools glibc-doc python-setuptools Recommended packages: manpages-dev libssl-doc The following NEW packages will be installed: augeas-lenses binutils cpp cpp-5 gcc gcc-5 libasan2 libatomic1 libaugeas0 libc-dev-bin libc6-dev libcc1-0 libcilkrts5 libexpat1-dev libffi-dev libgcc-5-dev libgomp1 libisl15 libitm1 liblsan0 libmpc3 libmpx0 libpython-dev libpython2.7 libpython2.7-dev libquadmath0 libssl-dev libtsan0 libubsan0 linux-libc-dev python-dev python-pip-whl python-pkg-resources python-virtualenv python2.7-dev python3-virtualenv virtualenv zlib1g-dev 0 upgraded, 38 newly installed, 0 to remove and 19 not upgraded. Need to get 57.9 MB of archives. After this operation, 154 MB of additional disk space will be used. Do you want to continue? [Y/n] нажимаю клавишу «Y»
в этот момент устанавливаю дополнительные пакеты необходимые для работы данного скрипта (certbot-auto). Ожидаю.
На заметку: Web-сервис уже должен быть установлен: nginx or apache2.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator nginx, Installer nginx
Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): support@ekzorchik.ru
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Which names would you like to activate HTTPS for?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: creative-impulse.ru
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): нажимаю клавишу Enter
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for creative-impulse.ru
Waiting for verification...
Cleaning up challenges
Deploying Certificate to VirtualHost /etc/nginx/sites-enabled/creative-impulse.ru
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Redirecting all traffic on port 80 to ssl in /etc/nginx/sites-enabled/creative-impulse.ru
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
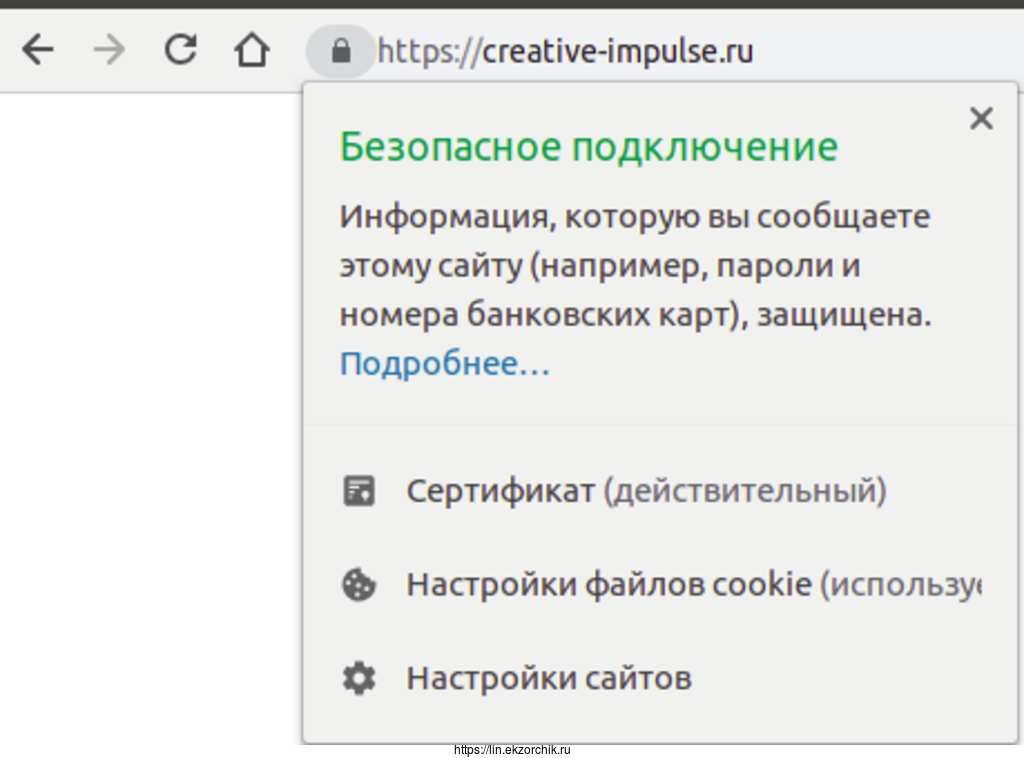
Congratulations! You have successfully enabled https://creative-impulse.ru
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=creative-impulse.ru
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/creative-impulse.ru/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/creative-impulse.ru/privkey.pem
Your cert will expire on 2019-05-03. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again with the "certonly" option. To non-interactively renew *all*
of your certificates, run "certbot-auto renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
ekzorchik@creative-impulse:~$ sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 2048
ekzorchik@creative-impulse:~$ sudo nano /etc/nginx/sites-enabled/creative-impulse.ru
server {
listen 80;
server_name creative-impulse.ru;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
server_name creative-impulse.ru;
ssl_certificate /etc/letsencrypt/live/creative-impulse.ru/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/creative-impulse.ru/privkey.pem;
include /etc/letsencrypt/options-ssl-nginx.conf;
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem;
root /var/www/html/wordpress;
index index.php;
access_log /var/www/html/wordpress/logs/access.log;
error_log /var/www/html/wordpress/logs/error.log;
location / {
try_files $uri $uri/ /index.php?$args;
}
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/run/php/php7.0-fpm.sock;
gzip on; #
gzip_disable "msie6";
gzip_types text/plain text/css application/json application/x-javascript text/xml application/xml application/xml+rss text/javascript application/javascript;
location ~ /\. {
deny all;
}
location ~ /.well-known {
allow all;
}
location ~* /(?:uploads|files)/.*\.php$ {
deny all;
}
location ~* ^.+\.(ogg|ogv|svg|svgz|eot|otf|woff|mp4|ttf|rss|atom|jpg|jpeg|gif|png|ico|zip|tgz|gz|rar|bz2|doc|xls|exe|ppt|tar|mid|midi|wav|bmp|rtf)$ {
access_log off;
log_not_found off;
expires max;
}
}
}
ekzorchik@creative-impulse:~$ sudo nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
ekzorchik@creative-impulse:~$ sudo systemctl restart nginx
ekzorchik@creative-impulse:~$ sudo systemctl status nginx | head -n5
● nginx.service - A high performance web server and a reverse proxy server
Loaded: loaded (/lib/systemd/system/nginx.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2019-02-04 13:41:15 MSK; 9s ago
Process: 19011 ExecStop=/sbin/start-stop-daemon --quiet --stop --retry QUIT/5 --pidfile /run/nginx.pid (code=exited, status=0/SUCCESS)
Process: 19020 ExecStart=/usr/sbin/nginx -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Проверка сертификата на сайте:
https://www.ssllabs.com/ssltest/analyze.html?d=creative-impulse.ru&latest
и вот только вот этими действиями выше у меня заработало:
ekzorchik@creative-impulse:~$ free -m total used free shared buff/cache available Mem: 992 129 156 26 705 668 Swap: 1019 0 1019
Чтобы сертификат автоматически перевыпускался каждые 3 месяца:
ekzorchik@creative-impulse:~$ sudo crontab -e 0 2 * * * sudo /usr/sbin/certbot-auto -q renew
Проверил данную инструкцию от 04.02.2019 и шаг за шагом она заработала, также она пригодилась когда переносил рабочий портал dealers.ekzorchik.ru & customizer.ekzorchik.ru. Вот что значит сделать один раз и после использовать постоянно.
От 13.07.2020
asivkov@srv-web01 (08:40:56 13/07/2020)
привет! dealers.ekzorchik.ru — выдает ошибку сертификата
asivkov@srv-web01 (08:41:28 13/07/2020)
посмотрел — сертификат истек вчера
странно что не отработало обновление сертификата.
aollo@ekzorchik:~$ sudo /usr/local/sbin/certbot-auto -q renew
Couldn’t download https://raw.githubusercontent.com/certbot/certbot/v1.6.0/letsencrypt-auto-source/letsencrypt-auto. HTTP Error 500: Internal Server Error
aollo@ekzorchik:~$ certbot-auto —version
Requesting to rerun /usr/local/sbin/certbot-auto with root privileges…
Upgrading certbot-auto 1.3.0 to 1.6.0…
Replacing certbot-auto…
Creating virtual environment…
Installing Python packages…
Installation succeeded.
certbot 1.6.0
aollo@ekzorchik:~$ sudo /usr/local/sbin/certbot-auto -q renew
изменилась версия утилиты и поэтому не отработала утилита, обновил и сертификат продлился на 90 дней
На этом у меня всё, с уважением автор блога Олло Александр aka ekzorchik.